CSO Online
Dark Reading
Dark Web Informer
Europol
Krebs on Security
NSA
Reuters
Security Affairs
The Hacker News
Wired
ZDNET
Security-Tools für KI-Infrastrukturen – ein Kaufratgeber
Tue Mar 10 2026
Tools, die die KI-Infrastruktur unter die Lupe nehmen, optimieren und absichern, liegen im Trend.
CSO Online
FBI alert: scammers target zoning permit applicants
Mon Mar 09 2026
The FBI warns of phishing attacks where crooks impersonate U.S. city and county officials to target people requesting planning and zoning permits. The FBI warns that scammers are impersonating U.S. city and county officials in phishing campaigns targeting businesses and individuals applying for planning or zoning permits. Using publicly available information, attackers craft messages that […]
Security Affairs

Hacker abusing .arpa domain to evade phishing detection, says Infoblox
Tue Mar 10 2026
A threat actor has found a new way to evade phishing detection defenses: Manipulate the .
CSO Online
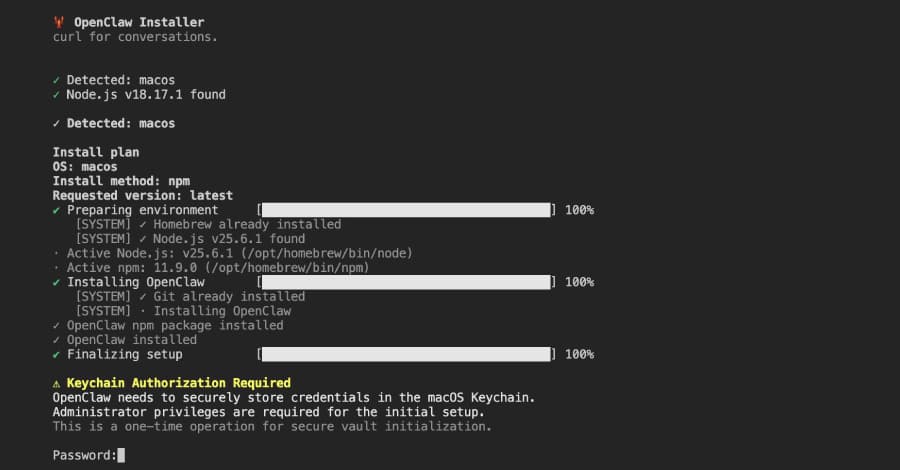
Malicious npm Package Posing as OpenClaw Installer Deploys RAT, Steals macOS Credentials
Mon Mar 09 2026
Cybersecurity researchers have discovered a malicious npm package that masquerades as an OpenClaw installer to deploy a remote access trojan (RAT) and steal sensitive data from compromised hosts. The package, named "@openclaw-ai/openclawai," was uploaded to the registry by a user named "openclaw-ai" on March 3, 2026. It has been downloaded 178 times to date. The library is still available for...
The Hacker News

CVE program funding secured, easing fears of repeat crisis
Mon Mar 09 2026
The Cybersecurity and Infrastructure Security Agency and the MITRE Corporation have renegotiated the contract supporting the 26-year-old Common Vulnerabilities and Exposures Program in a way that elim
CSO Online
Russia-linked hackers target Signal, WhatsApp of officials globally
Mon Mar 09 2026
Russia-linked hackers are targeting Signal and WhatsApp accounts of government and military officials worldwide, warns Dutch intelligence. Dutch intelligence agencies (MIVD and AIVD) warn of a global campaign by Russia-linked threat actors aiming to compromise Signal and WhatsApp accounts. The operation targets government officials, civil servants, and military personnel, highlighting growing cyber risks to sensitive […]
Security Affairs

UNC4899 Breached Crypto Firm After Developer AirDropped Trojanized File to Work Device
Mon Mar 09 2026
The North Korean threat actor known as UNC4899 is suspected to be behind a sophisticated cloud compromise campaign targeting a cryptocurrency organization in 2025 to steal millions of dollars in cryptocurrency. The activity has been attributed with moderate confidence to the state-sponsored adversary, which is also tracked under the cryptonyms Jade Sleet, PUKCHONG, Slow Pisces, and...
The Hacker News

⚡ Weekly Recap: Qualcomm 0-Day, iOS Exploit Chains, AirSnitch Attack & Vibe-Coded Malware
Mon Mar 09 2026
Another week in cybersecurity. Another week of "you've got to be kidding me." Attackers were busy. Defenders were busy. And somewhere in the middle, a whole lot of people had a very bad Monday morning. That's kind of just how it goes now. The good news? There were some actual wins this week. Real ones. The kind where the good guys showed up, did the work, and made a dent. It doesn't always...
The Hacker News

OpenAI says Codex Security found 11,000 high-impact bugs in a month
Mon Mar 09 2026
OpenAI’s new AppSec agent, Codex Security, has already flagged over 11,000 high-severity and critical flaws in real-world codebases during its first 30 days of research testing.
CSO Online
Cognizant’s TriZetto Provider Solutions data breach impacted over 3.4 million patients
Mon Mar 09 2026
A breach at Cognizant’s TriZetto Provider Solutions exposed sensitive health data belonging to more than 3.4 million patients. A data breach at Cognizant’s TriZetto Provider Solutions exposed sensitive information belonging to more than 3.4 million patients. At this time, no ransomware group has claimed responsibility for the attack yet. TriZetto Provider Solutions is a healthcare […]
Security Affairs

Can the Security Platform Finally Deliver for the Mid-Market?
Mon Mar 09 2026
Mid-market organizations are constantly striving to achieve security levels on a par with their enterprise peers. With heightened awareness of supply chain attacks, your customers and business partners are defining the security level you must meet. What if you could be the enabler for your organization to remain competitive — and help win business — by easily demonstrating that you meet these...
The Hacker News

NIS-2: Tausende reißen BSI-Frist und riskieren Strafen
Mon Mar 09 2026
Das deutsche Gesetz zur Umsetzung der NIS-2-Richtlinie ist am 6.
CSO Online

Chrome Extension Turns Malicious After Ownership Transfer, Enabling Code Injection and Data Theft
Mon Mar 09 2026
Two Google Chrome extensions have turned malicious after what appears to be a case of ownership transfer, offering attackers a way to push malware to downstream customers, inject arbitrary code, and harvest sensitive data. The extensions in question, both originally associated with a developer named "akshayanuonline@gmail.com" (BuildMelon), are listed below - QuickLens - Search Screen with...
The Hacker News
Anthropic Claude Opus AI model discovers 22 Firefox bugs
Mon Mar 09 2026
Anthropic used Claude Opus 4.6 to identify 22 Firefox vulnerabilities, most of which were high severity, all of which were fixed in Firefox 148, released in January 2026. Anthropic discovered 22 security vulnerabilities in Firefox using its Claude Opus 4.6 AI model in January 2026. Mozilla addressed these issues in Firefox 148. The researchers state […]
Security Affairs

Rogues gallery: 15 worst ransomware groups active today
Mon Mar 09 2026
Ransomware-as-a-service (RaaS) models, double extortion tactics, and increasing adoption of AI characterize the evolving ransomware threat landscape.
CSO Online
Web Server Exploits and Mimikatz Used in Attacks Targeting Asian Critical Infrastructure
Mon Mar 09 2026
High-value organizations located in South, Southeast, and East Asia have been targeted by a Chinese threat actor as part of a years-long campaign. The activity, which has targeted aviation, energy, government, law enforcement, pharmaceutical, technology, and telecommunications sectors, has been attributed by Palo Alto Networks Unit 42 to a previously undocumented threat activity group dubbed...
The Hacker News

4 ways to prepare your SOC for agentic AI
Mon Mar 09 2026
a way to automate alert triage, threat investigation and eventually higher-level functions.
CSO Online
How AI Assistants are Moving the Security Goalposts
Sun Mar 08 2026
AI-based assistants or "agents" -- autonomous programs that have access to the user's computer, files, online services and can automate virtually any task -- are growing in popularity with developers and IT workers. But as so many eyebrow-raising headlines over the past few weeks have shown, these powerful and assertive new tools are rapidly shifting the security priorities for organizations, while blurring the lines between data and code, trusted co-worker and insider threat, ninja hacker and novice code jockey.
Krebs on Security
Critical Nginx UI flaw CVE-2026-27944 exposes server backups
Sun Mar 08 2026
Nginx UI flaw CVE-2026-27944 lets attackers download and decrypt server backups without authentication, exposing sensitive data on public management interfaces. A critical vulnerability in Nginx UI, tracked as CVE-2026-27944 (CVSS score of 9.8), allows attackers to download and decrypt full server backups without authentication. The flaw poses a serious risk to organizations exposing the management […]
Security Affairs
Massive GitHub malware operation spreads BoryptGrab stealer
Sun Mar 08 2026
Trend Micro found BoryptGrab stealer spreading through 100+ GitHub repositories, stealing browser data, crypto wallets, system information, and user files. Trend Micro uncovered a campaign distributing the BoryptGrab information stealer through more than 100 GitHub repositories. BoryptGrab is designed to collect browser and cryptocurrency wallet data, system details, and common files. Some variants also deploy […]
Security Affairs
SECURITY AFFAIRS MALWARE NEWSLETTER ROUND 87
Sun Mar 08 2026
Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape Malware Newsletter Malware Reverse Engineering is no longer a human problem! StegaBin: 26 Malicious npm Packages Use Pastebin Steganography to Deploy Multi-Stage Credential Stealer Inside a fake Google security check that becomes a browser RAT SloppyLemming […]
Security Affairs
Security Affairs newsletter Round 566 by Pierluigi Paganini – INTERNATIONAL EDITION
Sun Mar 08 2026
A new round of the weekly Security Affairs newsletter has arrived! Every week, the best security articles from Security Affairs are free in your email box. Enjoy a new round of the weekly SecurityAffairs newsletter, including the international press. FBI probing intrusion into a system managing sensitive surveillance information Reading White House President Trump’s Cyber […]
Security Affairs
FBI probing intrusion into a system managing sensitive surveillance information
Sat Mar 07 2026
The Federal Bureau of Investigation (FBI) is probing suspicious activity on an internal system containing sensitive surveillance and investigation data. The FBI is investigating suspicious cyber activity affecting an internal system that stores sensitive data tied to surveillance operations and investigations, The Associated Press reports. According to a notification sent to members of the United […]
Security Affairs
Reading White House President Trump’s Cyber Strategy for America (March 2026)
Sat Mar 07 2026
White House released President Trump’s Cyber Strategy for America, framing cyberspace as a strategic domain to project power and counter growing cyber threats The White House has released “President Trump’s Cyber Strategy for America,” a document that outlines how the United States intends to maintain dominance in cyberspace and confront an increasingly hostile digital landscape. […]
Security Affairs

PQC roadmap remains hazy as vendors race for early advantage
Mon Mar 09 2026
Post-quantum cryptography (PQC) has long sat on the periphery of enterprise security, with experts calling it inevitable but not urgent.
CSO Online

Tarnung als Taktik: Warum Ransomware-Angriffe raffinierter werden
Mon Mar 09 2026
Statt eines kurzen, aber sehr schmerzhaften Stiches setzen Cyberkrimelle zunehmend darauf, sich in ihren Opfern festzubeißen und beständig auszusaugen.
CSO Online
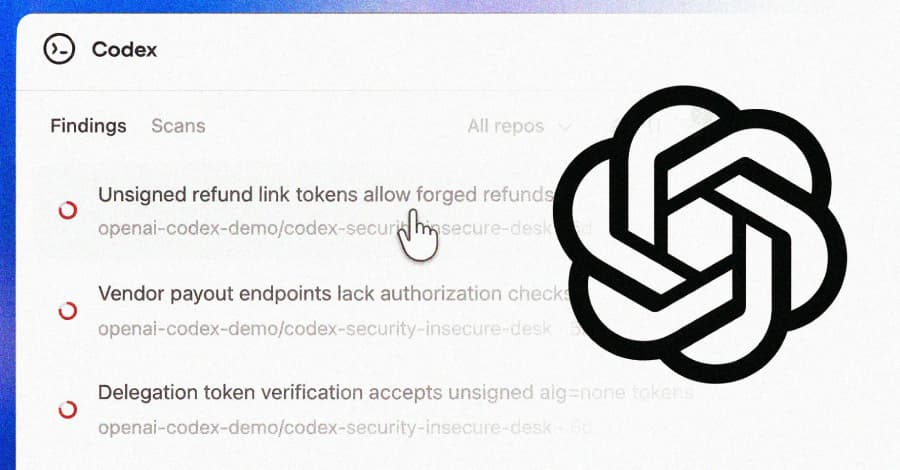
OpenAI Codex Security Scanned 1.2 Million Commits and Found 10,561 High-Severity Issues
Sat Mar 07 2026
OpenAI on Friday began rolling out Codex Security, an artificial intelligence (AI)-powered security agent that's designed to find, validate, and propose fixes for vulnerabilities. The feature is available in a research preview to ChatGPT Pro, Enterprise, Business, and Edu customers via the Codex web with free usage for the next month. "It builds deep context about your project to identify...
The Hacker News
CBP Used Online Ad Data to Track Phone Locations
Sat Mar 07 2026
Plus: Proton helped the FBI identify a protester, the Leakbase cybercrime forum was busted in an international operation, and more.
Wired

Anthropic Finds 22 Firefox Vulnerabilities Using Claude Opus 4.6 AI Model
Sat Mar 07 2026
Anthropic on Friday said it discovered 22 new security vulnerabilities in the Firefox web browser as part of a security partnership with Mozilla. Of these, 14 have been classified as high, seven have been classified as moderate, and one has been rated low in severity. The issues were addressed in Firefox 148, released late last month. The vulnerabilities were identified over a two-week period in...
The Hacker News

How Each Gulf Country Is Intercepting Iranian Missiles and Drones
Sat Mar 07 2026
As missiles and drones cross the region’s skies, the Gulf’s layered air-defense networks—from THAAD to Patriot batteries—are being tested in real time.
Wired
Iran-linked hackers target IP cameras across Israel and Gulf states for military intelligence
Sat Mar 07 2026
Researchers observed Iran-linked actors targeting IP cameras across Israel and Gulf countries, likely to support military intelligence and battle damage assessment. According to the Check Point Cyber Security Report 2026, cyber operations are increasingly used to support military activity and battle damage assessment (BDA). During the Israel-Iran tensions, researchers from Check Point Software Technologies observed […]
Security Affairs

Trump’s cyber strategy emphasizes offensive operations, deregulation, AI
Fri Mar 06 2026
The White House released President Donald Trump’s long-awaited cybersecurity strategy, a lean seven-page blueprint that breaks from past approaches by placing offensive cyber operations at the center
CSO Online

ClickFix attackers using new tactic to evade detection, says Microsoft
Fri Mar 06 2026
Threat actors are trying a different tactic to sucker employees into falling for ClickFix phishing attacks that install malware, says Microsoft.
CSO Online

The Future of Iran’s Internet Is More Uncertain Than Ever
Fri Mar 06 2026
Iran’s internet shutdown has reduced connectivity by 99 percent, with air strikes likely causing additional outages, and few workarounds remaining.
Wired
Iran-linked MuddyWater deploys Dindoor malware against U.S. organizations
Fri Mar 06 2026
Iran-linked APT MuddyWater targeted U.S. organizations, deploying the new Dindoor backdoor across sectors including banks, airports, and nonprofits. Broadcom’s Symantec Threat Hunter Team uncovered a campaign by the Iran-linked MuddyWater (aka SeedWorm, TEMP.Zagros, Mango Sandstorm, TA450, and Static Kitten) APT group targeting several U.S. organizations. “Activity associated with Iranian APT group Seedworm has been spotted on the networks of multiple […]
Security Affairs

Only 30 minutes per quarter on cyber risk: Why CISO-board conversations are falling short
Fri Mar 06 2026
Cybersecurity is, as it should be in this era of AI-driven cyberattacks, a regular item on enterprise board agendas.
CSO Online

FBI wiretap system tapped by hackers
Fri Mar 06 2026
The US Federal Bureau of Investigation (FBI) has identified a suspected incident on a network used to manage wiretaps and foreign intelligence surveillance warrants, CNN reported.
CSO Online

OAuth vulnerability in n8n automation platform could lead to system compromise
Fri Mar 06 2026
A weakness in the configuration of OAuth credentials opens up a stored XSS vulnerability in the n8n automation platform, researchers at Imperva have discovered.
CSO Online
Cisco flags ongoing exploitation of two recently patched Catalyst SD-WAN flaws
Fri Mar 06 2026
Cisco warns that two recently patched Catalyst SD-WAN flaws, CVE-2026-20128 and CVE-2026-20122, are already being actively exploited in the wild. Cisco warned customers that threat actors are actively exploiting two recently patched Catalyst SD-WAN vulnerabilities, CVE-2026-20128 and CVE-2026-20122. The networking giant urged organizations to apply the latest security updates to reduce the risk of compromise. […]
Security Affairs

Transparent Tribe Uses AI to Mass-Produce Malware Implants in Campaign Targeting India
Fri Mar 06 2026
The Pakistan-aligned threat actor known as Transparent Tribe has become the latest hacking group to embrace artificial intelligence (AI)-powered coding tools to strike targets with various implants. The activity is designed to produce a "high-volume, mediocre mass of implants" that are developed using lesser-known programming languages like Nim, Zig, and Crystal and rely on trusted services like...
The Hacker News

Multi-Stage VOID#GEIST Malware Delivering XWorm, AsyncRAT, and Xeno RAT
Fri Mar 06 2026
Cybersecurity researchers have disclosed details of a multi-stage malware campaign that uses batch scripts as a pathway to deliver various encrypted remote access trojan (RATs) payloads that correspond to XWorm, AsyncRAT, and Xeno RAT. The stealthy attack chain has been codenamed VOID#GEIST by Securonix Threat Research. At a high level, the obfuscated batch script is used to deploy a second...
The Hacker News

Targeted advertising is also targeting malware
Fri Mar 06 2026
Online ads are increasingly being used a means of introducing malware into organizations, according to The Media Trust.
CSO Online
Microsoft warns of ClickFix campaign exploiting Windows Terminal to deliver Lumma Stealer
Fri Mar 06 2026
Microsoft warns of ClickFix campaign using Windows Terminal to deliver Lumma Stealer via social engineering attacks. Microsoft revealed a new ClickFix campaign where attackers exploit Windows Terminal to run a complex attack chain, ultimately deploying Lumma Stealer malware. The campaign uses social engineering to trick users into executing malicious commands, highlighting growing risks to Windows […]
Security Affairs

From Ukraine to Iran, Hacking Security Cameras Is Now Part of War’s ‘Playbook’
Fri Mar 06 2026
New research shows hundreds of attempts by apparent Iranian state hackers to hijack consumer-grade cameras, timed to missile and drone strikes. Israel, Russia, and Ukraine have also adopted this trick.
Wired

The MSP Guide to Using AI-Powered Risk Management to Scale Cybersecurity
Fri Mar 06 2026
Scaling cybersecurity services as an MSP or MSSP requires technical expertise and a business model that delivers measurable value at scale. Risk-based cybersecurity is the foundation of that model. When done right, it builds client trust, increases upsell opportunities, and drives recurring revenue. But to deliver this consistently and efficiently, you need the right technology and processes....
The Hacker News

Iran-Linked MuddyWater Hackers Target U.S. Networks With New Dindoor Backdoor
Fri Mar 06 2026
New research from Broadcom's Symantec and Carbon Black Threat Hunter Team has discovered evidence of an Iranian hacking group embedding itself in several U.S. companies' networks, including banks, airports, non-profit, and the Israeli arm of a software company. The activity has been attributed to a state-sponsored hacking group called MuddyWater (aka Seedworm). It's affiliated with the Iranian...
The Hacker News
Iran-nexus APT Dust Specter targets Iraq officials with new malware
Fri Mar 06 2026
A campaign by Iran-linked group Dust Specter is targeting Iraqi officials with phishing emails delivering new malware families. Zscaler ThreatLabz researchers linked the Iran-nexus group Dust Specter to a campaign targeting Iraqi government officials. Threat actors impersonated the country’s Ministry of Foreign Affairs in phishing messages that delivered previously unseen malware, including SPLITDROP, TWINTASK, TWINTALK, […]
Security Affairs
U.S. CISA adds Apple, Rockwell, and Hikvision flaws to its Known Exploited Vulnerabilities catalog
Fri Mar 06 2026
U.S. Cybersecurity and Infrastructure Security Agency (CISA) adds Apple, Rockwell, and Hikvision flaws to its Known Exploited Vulnerabilities catalog. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) added Apple, Rockwell, and Hikvision flaws to its Known Exploited Vulnerabilities (KEV) catalog. Below are the flaws added to the catalog: CVE-2023-43000 is a use-after-free issue in the WebKit component. Apple […]
Security Affairs

Teenage hacker myth primed for a middle-age criminal makeover
Fri Mar 06 2026
The Hollywood image of criminal hackers being largely teenage ne’er do wells is due for an update.
CSO Online
China-Linked Hackers Use TernDoor, PeerTime, BruteEntry in South American Telecom Attacks
Fri Mar 06 2026
A China-linked advanced persistent threat (APT) actor has been targeting critical telecommunications infrastructure in South America since 2024, targeting Windows and Linux systems and edge devices with three different implants. The activity is being tracked by Cisco Talos under the moniker UAT-9244, describing it as closely associated with another cluster known as FamousSparrow. It's worth...
The Hacker News

Challenges and projects for the CISO in 2026
Fri Mar 06 2026
Sophisticated attacks and the incorporation of AI tools, talent shortages, and tight budgets are some of the challenges commonly cited when it comes to managing cybersecurity in organizations.
CSO Online
Google GTIG: 90 zero-day flaws exploited in 2025 as enterprise targets grow
Fri Mar 06 2026
Google’s GTIG reports 90 zero-day vulnerabilities exploited in the wild in 2025, up from 78 in 2024, with a growing share targeting enterprise systems. Google’s Threat Intelligence Group (GTIG) identified 90 zero-day vulnerabilities exploited in the wild in 2025. While slightly below the 100 observed in 2023, the number increased from 78 in 2024, with […]
Security Affairs

Zero-day exploits hit enterprises faster and harder
Fri Mar 06 2026
Google tracked 90 vulnerabilities exploited as zero-days last year, with Chinese cyberespionage groups doubling their count from 2024 and commercial surveillance vendors overtaking state-sponsored hac
CSO Online
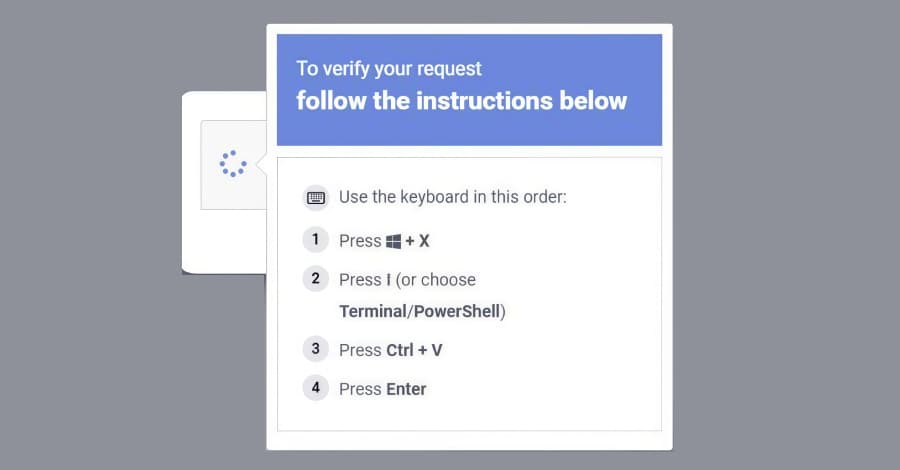
Microsoft Reveals ClickFix Campaign Using Windows Terminal to Deploy Lumma Stealer
Fri Mar 06 2026
Microsoft on Thursday disclosed details of a new widespread ClickFix social engineering campaign that has leveraged the Windows Terminal app as a way to activate a sophisticated attack chain and deploy the Lumma Stealer malware. The activity, observed in February 2026, makes use of the terminal emulator program instead of instructing users to launch the Windows Run dialog and paste a command...
The Hacker News
Hikvision and Rockwell Automation CVSS 9.8 Flaws Added to CISA KEV Catalog
Fri Mar 06 2026
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday added two security flaws impacting Hikvision and Rockwell Automation products to its Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation. The critical-severity vulnerabilities are listed below - CVE-2017-7921 (CVSS score: 9.8) - An improper authentication vulnerability affecting...
The Hacker News

Europa im Visier von Cyber-Identitätsdieben
Fri Mar 06 2026
Deutsche Unternehmen müssen sich warm anziehen: Sowohl staatliche als auch „private“ Akteure haben es auf sie abgesehen.
CSO Online

7 Anzeichen für akuten MSSP-Bedarf
Fri Mar 06 2026
Managed Security Service Provider können das Sicherheitsniveau nachhaltig steigern.
CSO Online

LeakBase marketplace unplugged by cops in 14 countries
Fri Mar 06 2026
The LeakBase cyberforum, considered one of the world’s largest online marketplaces for cybercriminals to buy and sell stolen data and cybercrime tools, has been seized by the US, and arrests have also
CSO Online
Phobos Ransomware admin faces up to 20 years after guilty plea
Thu Mar 05 2026
Russian national Evgenii Ptitsyn (43) pleaded guilty in the U.S. for his role in the Phobos ransomware operation. Russian national Evgenii Ptitsyn pleaded guilty in the US to wire fraud conspiracy for his role in the Phobos ransomware scheme. The man was arrested in South Korea in 2024 and extradited to the United States. He […]
Security Affairs
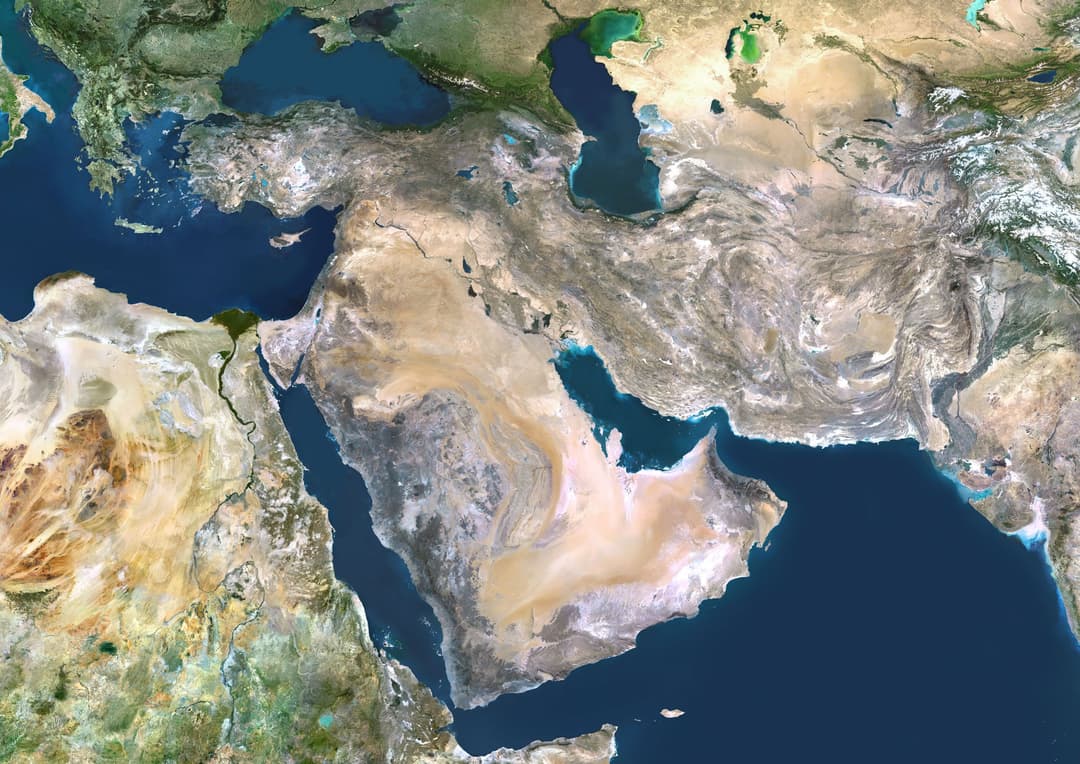
Here’s Every Country Directly Impacted by the War on Iran
Thu Mar 05 2026
As the conflict in the Middle East continues to escalate, more than a dozen countries in the region have reportedly been affected by air strikes.
Wired

The Controversies Finally Caught Up to Kristi Noem
Thu Mar 05 2026
Donald Trump said he would replace the secretary of the Department of Homeland Security. Noem’s tenure was marked by aggressive anti-immigration tactics and ICE and CBP’s killing of two US protesters.
Wired

Cisco issues emergency patches for critical firewall vulnerabilities
Thu Mar 05 2026
Cisco has handed security teams one of the largest ever patching workloads affecting its firewall products, including fixes for two ‘perfect 10’ vulnerabilities in the company’s Secure Firewall Manage
CSO Online
Russian APT targets Ukraine with BadPaw and MeowMeow malware
Thu Mar 05 2026
Researchers uncovered a Russian campaign targeting Ukrainian entities with new malware families BadPaw and MeowMeow delivered through phishing emails. Researchers reported a phishing campaign linked to Russia that targets Ukrainian organizations using two new malware families, BadPaw and MeowMeow. The attack chain begins with a phishing email carrying a link to a ZIP archive. When […]
Security Affairs

Cisco Confirms Active Exploitation of Two Catalyst SD-WAN Manager Vulnerabilities
Thu Mar 05 2026
Cisco has disclosed that two more vulnerabilities affecting Catalyst SD-WAN Manager (formerly SD-WAN vManage) have come under active exploitation in the wild. The vulnerabilities in question are listed below - CVE-2026-20122 (CVSS score: 7.1) - An arbitrary file overwrite vulnerability that could allow an authenticated, remote attacker to overwrite arbitrary files on the local file system....
The Hacker News
Preparing for the Quantum Era: Post-Quantum Cryptography Webinar for Security Leaders
Thu Mar 05 2026
Most organizations assume encrypted data is safe. But many attackers are already preparing for a future where today’s encryption can be broken. Instead of trying to decrypt information now, they are collecting encrypted data and storing it so it can be decrypted later using quantum computers. This tactic—known as “harvest now, decrypt later”—means sensitive data transmitted today could become...
The Hacker News

Coruna iOS exploit kit moved from spy tool to mass criminal campaign in under a year
Thu Mar 05 2026
Google’s threat intelligence researchers have identified a sophisticated exploit kit targeting iPhones that was first used by a commercial surveillance vendor’s customer before being repurposed by a s
CSO Online

ThreatsDay Bulletin: DDR5 Bot Scalping, Samsung TV Tracking, Reddit Privacy Fine & More
Thu Mar 05 2026
Some weeks in cybersecurity feel routine. This one doesn’t. Several new developments surfaced over the past few days, showing how quickly the threat landscape keeps shifting. Researchers uncovered fresh activity, security teams shared new findings, and a few unexpected moves from major tech companies also drew attention. Together, these updates offer a useful snapshot of what is happening...
The Hacker News

Europol: Großer Markt für gestohlene Daten geschlossen
Thu Mar 05 2026
Europol koordinierte den Schlag gegen Leakbase.
CSO Online

Dust Specter Targets Iraqi Officials with New SPLITDROP and GHOSTFORM Malware
Thu Mar 05 2026
A suspected Iran-nexus threat actor has been attributed to a campaign targeting government officials in Iraq by impersonating the country's Ministry of Foreign Affairs to deliver a set of never-before-seen malware. Zscaler ThreatLabz, which observed the activity in January 2026, is tracking the cluster under the name Dust Specter. The attacks, which manifest in the form of two different...
The Hacker News
Europol schließt riesigen Markt für gestohlene Daten
Thu Mar 05 2026
loading="lazy" width="400px">LeakBase wird von den Strafverfolgungsbehörden untersucht.
CSO Online

Where Multi-Factor Authentication Stops and Credential Abuse Starts
Thu Mar 05 2026
Organizations typically roll out multi-factor authentication (MFA) and assume stolen passwords are no longer enough to access systems. In Windows environments, that assumption is often wrong. Attackers still compromise networks every day using valid credentials. The issue is not MFA itself, but coverage. Enforced through an identity provider (IdP) such as Microsoft Entra ID, Okta, or...
The Hacker News

APT28-Linked Campaign Deploys BadPaw Loader and MeowMeow Backdoor in Ukraine
Thu Mar 05 2026
Cybersecurity researchers have disclosed details of a new Russian cyber campaign that has targeted Ukrainian entities with two previously undocumented malware families named BadPaw and MeowMeow. "The attack chain initiates with a phishing email containing a link to a ZIP archive. Once extracted, an initial HTA file displays a lure document written in Ukrainian concerning border crossing appeals...
The Hacker News
.jpg&w=1080&q=75)
How a Music Streaming CEO Built an Open-Source Global Threat Map in His Spare Time
Thu Mar 05 2026
Frustrated by fragmented war news, Anghami’s Elie Habib built World Monitor, a platform that fuses global data, like aircraft signals and satellite detections, to track conflicts as they unfold.
Wired
Operation Leak: FBI and Europol dismantle LeakBase Cybercrime forum
Thu Mar 05 2026
The Federal Bureau of Investigation seized the LeakBase cybercrime forum in an international crackdown led by Europol. The Federal Bureau of Investigation seized the LeakBase cybercrime forum (leakbase[.]la), a platform used to trade hacking tools and stolen data. The action formed part of “Operation Leak,” an international effort coordinated by Europol involving authorities from 14 […]
Security Affairs

State-affiliated hackers set up for critical OT attacks that operators may not detect
Thu Mar 05 2026
Several state-linked threat groups known for breaking into operational technology (OT) networks have shifted their focus over the past year from gaining and maintaining access to actively mapping out
CSO Online

Europol-Led Operation Takes Down Tycoon 2FA Phishing-as-a-Service Linked to 64,000 Attacks
Thu Mar 05 2026
Tycoon 2FA, one of the prominent phishing-as-a-service (PhaaS) toolkits that allowed cybercriminals to stage adversary-in-the-middle (AitM) credential harvesting attacks at scale, was dismantled by a coalition of law enforcement agencies and security companies. The subscription-based phishing kit, which first emerged in August 2023, was described by Europol as one of the largest phishing...
The Hacker News
FBI and Europol Seize LeakBase Forum Used to Trade Stolen Credentials
Thu Mar 05 2026
A joint law enforcement operation has dismantled LeakBase, one of the world's largest online forums for cybercriminals to buy and sell stolen data and cybercrime tools. The LeakBase forum, per the U.S. Department of Justice (DoJ), had over 142,000 members and more than 215,000 messages between members as of December 2025. Those attempting to access the forum's website ("leakbase[.]la") are now...
The Hacker News
Google uncovers Coruna iOS Exploit Kit targeting iOS 13–17.2.1
Thu Mar 05 2026
Google warns of the Coruna iOS exploit kit, using 23 exploits across five chains to target iPhones running iOS 13–17.2.1, but not the latest iOS. Google’s Threat Intelligence Group has identified a powerful new iOS exploit kit called Coruna (also known as CryptoWaters) that targets Apple iPhones running iOS versions 13.0 through 17.2.1. The kit […]
Security Affairs

14 old software bugs that took way too long to squash
Thu Mar 05 2026
In 2021, a vulnerability was revealed in a system that lay at the foundation of modern computing.
CSO Online

Die besten Cyber-Recovery-Lösungen
Thu Mar 05 2026
Nicht greifende Recovery-Prozesse sind für Unternehmen ein Albtraumszenario, das dank ausgefeilter Angriffe immer öfter zur Realität wird.
CSO Online

Microsoft leads takedown of Tycoon2FA phishing service infrastructure
Thu Mar 05 2026
The infrastructure hosting the Tycoon2FA service, which Europol said was among the largest phishing operations worldwide, has been taken down by a coalition of IT companies and law enforcement agencie
CSO Online
Cisco fixes maximum-severity Secure FMC bugs threatening firewall security
Wed Mar 04 2026
Cisco patched two critical Secure FMC vulnerabilities that could let attackers gain root access to managed firewalls. Cisco addressed two maximum-severity vulnerabilities in its Secure Firewall Management Center (FMC) that could allow attackers to gain root access. Cisco Secure Firewall Management Center (FMC) is a centralized management platform for Cisco firewalls. It lets administrators configure, […]
Security Affairs
Automate or orchestrate? Implementing a streamlined remediation program to shorten MTTR
Wed Mar 04 2026
Security teams want lower MTTR, but flaws persist. How to use automation vs. orchestration to reduce risk effectively? Almost all security teams want to reduce their Mean Time to Remediate (MTTR). And for good reason: research from 2024 found that it takes an average of 4.5 months to remediate critical vulnerabilities. The problem is that […]
Security Affairs
Why AI, Zero Trust, and modern security require deep visibility
Wed Mar 04 2026
AI.
CSO Online
The 10-hour problem: How visibility gaps are burning out the SOC
Wed Mar 04 2026
Security teams aren’t drowning because the threats improved.
CSO Online
LastPass warns of spoofed alerts aimed at stealing master passwords
Wed Mar 04 2026
LastPass warns of a phishing campaign using fake security alerts about unauthorized access or password changes to steal users’ master passwords. LastPass has warned users about a new phishing campaign using fake security alerts that claim unauthorized access or master password changes. The emails, which spoof LastPass’s display name, attempt to trick recipients into revealing […]
Security Affairs

How Vulnerable Are Computers to an 80-Year-Old Spy Technique? Congress Wants Answers
Wed Mar 04 2026
A pair of US lawmakers are calling for an investigation into how easily spies can steal information based on devices’ electromagnetic and acoustic leaks—a spying trick the NSA once codenamed TEMPEST.
Wired

149 Hacktivist DDoS Attacks Hit 110 Organizations in 16 Countries After Middle East Conflict
Wed Mar 04 2026
Cybersecurity researchers have warned of a surge in retaliatory hacktivist activity following the U.S.-Israel coordinated military campaign against Iran, codenamed Epic Fury and Roaring Lion. "The hacktivist threat in the Middle East is highly lopsided, with two groups, Keymous+ and DieNet, driving nearly 70% of all attack activity between February 28 and March 2," Radware said in a Tuesday...
The Hacker News
Coruna iOS Exploit Kit Uses 23 Exploits Across Five Chains Targeting iOS 13–17.2.1
Wed Mar 04 2026
Google said it identified a "new and powerful" exploit kit dubbed Coruna (aka CryptoWaters) targeting Apple iPhone models running iOS versions between 13.0 and 17.2.1. The exploit kit featured five full iOS exploit chains and a total of 23 exploits, Google Threat Intelligence Group (GTIG) said. It's not effective against the latest version of iOS. The findings were first reported by WIRED. "The...
The Hacker News
From phishing to Google Drive C2: Silver Dragon expands APT41 playbook
Wed Mar 04 2026
APT group Silver Dragon, linked to APT41, targets governments via server exploits and phishing, using Cobalt Strike and Google Drive for C2. Check Point researchers have identified Silver Dragon, an APT group tied to the China-linked group APT41, targeting government entities in Europe and Southeast Asia since mid-2024. The group gains initial access by exploiting […]
Security Affairs

Iranian cyberattacks fail to materialize but threat remains acute
Wed Mar 04 2026
Five days into US and Israel’s war with Iran, the worst predictions for cyber-retaliation have yet to materialize.
CSO Online
New RFP Template for AI Usage Control and AI Governance
Wed Mar 04 2026
As AI becomes the central engine for enterprise productivity, security leaders are finally getting the green light — and the budget — to secure it. But there’s a quiet crisis unfolding in the boardroom: many organizations know they need "AI Governance," but they have no idea what they are actually looking for. The CISO’s Dilemma: You Have the AI Budget, but Do You Have the Requirements? As AI...
The Hacker News

Fake Laravel Packages on Packagist Deploy RAT on Windows, macOS, and Linux
Wed Mar 04 2026
Cybersecurity researchers have flagged malicious Packagist PHP packages masquerading as Laravel utilities that act as a conduit for a cross-platform remote access trojan (RAT) that's functional on Windows, macOS, and Linux systems. The names of the packages are listed below - nhattuanbl/lara-helper (37 Downloads) nhattuanbl/simple-queue (29 Downloads) nhattuanbl/lara-swagger (49 Downloads)...
The Hacker News
U.S. CISA adds Qualcomm and Broadcom VMware Aria Operations flaws to its Known Exploited Vulnerabilities catalog
Wed Mar 04 2026
U.S. Cybersecurity and Infrastructure Security Agency (CISA) adds Qualcomm and Broadcom VMware Aria Operations flaws to its Known Exploited Vulnerabilities catalog. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) added Google Chromium CSS, Microsoft Windows, TeamT5 ThreatSonar Anti-Ransomware, and Zimbra flaws to its Known Exploited Vulnerabilities (KEV) catalog. Below are the flaws added to the catalog: In […]
Security Affairs
Data breach at University of Hawaiʻi Cancer Center impacts 1.2 Million individuals
Wed Mar 04 2026
A ransomware attack on the University of Hawaiʻi Cancer Center exposed personal data of 1.2 million people. A 2025 ransomware attack targeting the University of Hawaiʻi Cancer Center compromised the personal information of about 1.2 million individuals. The attack hit the University of Hawaiʻi Cancer Center on August 31, 2025, impacting servers that support research […]
Security Affairs

Anthropic AI ultimatums and IP theft: The unspoken risk
Wed Mar 04 2026
Two recent high-profile events concerning Anthropic’s Claude AI underscore a little-discussed risk at the heart of the enterprise’s rush to capitalize on leading AI capabilities.
CSO Online

APT41-Linked Silver Dragon Targets Governments Using Cobalt Strike and Google Drive C2
Wed Mar 04 2026
Cybersecurity researchers have disclosed details of an advanced persistent threat (APT) group dubbed Silver Dragon that has been linked to cyber attacks targeting entities in Europe and Southeast Asia since at least mid-2024. "Silver Dragon gains its initial access by exploiting public-facing internet servers and by delivering phishing emails that contain malicious attachments," Check Point said...
The Hacker News

How to know you’re a real-deal CSO — and whether that job opening truly seeks one
Wed Mar 04 2026
Recruiters of senior-level IT professionals often say that a truly skilled and experienced CSO is among the hardest of all IT roles to fill.
CSO Online

CISA Adds Actively Exploited VMware Aria Operations Flaw CVE-2026-22719 to KEV Catalog
Wed Mar 04 2026
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Tuesday added a recently disclosed security flaw impacting Broadcom VMware Aria Operations to its Known Exploited Vulnerabilities (KEV) catalog, citing active exploitation in the wild. The high-severity vulnerability, CVE-2026-22719 (CVSS score: 8.1), has been described as a case of command injection that could allow an...
The Hacker News

AI-powered attack kits go open source, and CyberStrikeAI may be just the beginning
Wed Mar 04 2026
AI is making it ever easier for bad actors to launch attacks, and a newly-identified open source platform, CyberStrikeAI, seems to be lowering the bar even further.
CSO Online